blog
Wordpress compromises: What's beyond the URL?
One of the many tricks in the modern cybercriminal miscreant's toolbox is using compromised websites to evade spam filters and domain reputation systems. Whether hiding a web-based exploit or just getting a free ride on the reputation of otherwise legitimate domains, using an existing domain name has multiple benefits –...
In this guide
Jump to
One of the many tricks in the modern cybercriminal miscreant's toolbox is using compromised websites to evade spam filters and domain reputation systems. Whether hiding a web-based exploit or just getting a free ride on the reputation of otherwise legitimate domains, using an existing domain name has multiple benefits – and that's not even taking into account the fact that stealing someone else's domain is cheaper than buying one. In this article we'll take a look beyond the URL of a compromised Wordpress website to provide some insight into what goes on once a website has been compromised.
Why Wordpress?
Many compromised sites turn out to be running Wordpress. Does this mean that Wordpress is a bad choice for a Content Management System (CMS)? No, Wordpress itself has improved greatly over the years and is in its default, out-of-the-box, state a solid and secure choice for many websites. This is supported that numbers show today over 40% of all websites worldwide run Wordpress. This vast market share means that there are many targets. Since these targets behave in a uniform way, it makes it attractive to develop tools to compromise them.
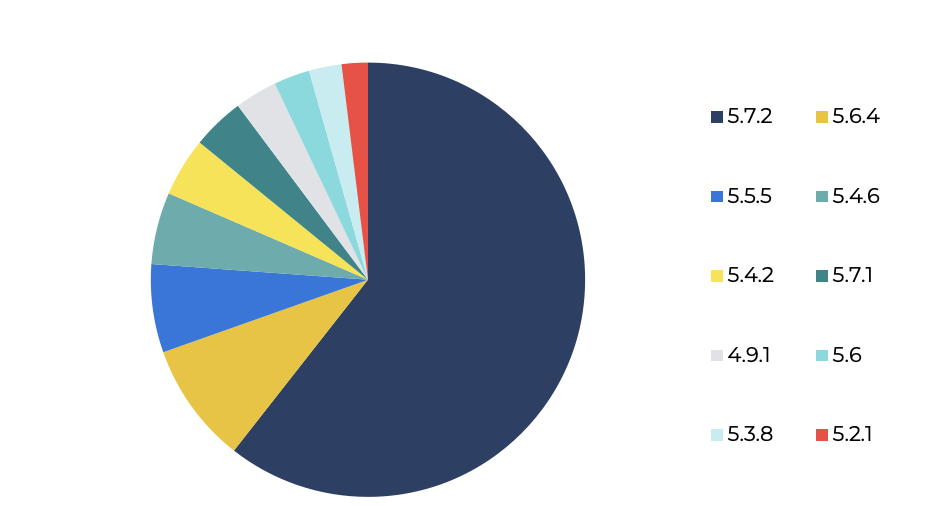
It is important to note that it is not just Wordpress itself that is targeted. Many of the problems are actually caused by plugins that are not kept up to date, or plugins that are already backdoored at the moment they are installed. The latter especially happens with pirated versions of paid-for plugins. When investigating this particular subset of compromised websites, we found that over half of them were running the latest stable version of Wordpress at the time of investigation. As they were still compromised almost certainly means that either the sites were compromised through a plugin, or that the attackers managed to maintain persistence on the targeted websites: the actual exploit was done in the past, but files placed by the attackers survived any updates.
Top 10 Wordpress versions seen on compromised websites
From exploit to platform
Eventually this toolchain becomes part of a bigger system, usually referred to by the miscreants as a TDS: Traffic Distribution System. This system manages the compromised sites, receives any hits from unsuspecting visitors and then serves them content based on pre-established parameters such as country of origin, browser type and operating system. Most TDS systems are a good example of how cybercrime facilitation has turned into the 'as a service' model: the group that runs the TDS sells capacity on the platform to other cybercriminals, to present their content to whatever demographic they may want to target. Some visitors may get a redirect to a casino website while others may be served a malicious browser plugin.
Spamhaus detects compromised websites being used in spam directly, or as part of a redirection chain, and adds the hostnames to our datasets to protect our users. As a result, the website's owners discover that they have a problem, and this is often where the more difficult part begins, as many of these Wordpress users do not have the skills to find out what is wrong and how to fix it.
Deceptive filenames
Initially, when the group exploits a WordPress website, they drop in 5-10 harmless-looking PHP files, with names like genericerror.php, email_friend.php or weblog_rss.php. The files are named in this fashion to avoid raising suspicion in case the webmaster decides to poke around his filesystem.
Source code obfuscation
If a curious admin decides to take a closer look at these files they will not find much readable code (which is a cause for alarm by itself!), since the files dropped by means of the exploit are obfuscated:
$uabeg="ttbttttattstttttetttt6ttttt4tttt_ttttdttttettttcttttottdttet"
$uu=str_ireplace("t","",$uabeg);
This is just the first layer: the str_ireplace command will replace all t's in the uabeg variable with nothing, leaving it to say base64_decode. This is another PHP command which will be used to decode further parts of the file. Only after 3 levels of 'decryption' is the first interesting information revealed: it leads to a configurable remote location for content. While the obfuscation is simple, it is effective in putting automated tools off-track.
Reverse proxy behavior
One of the interesting approaches in this particular case is that the files inserted into the compromised Wordpress instance are really just reverse proxies: they will funnel the received traffic to the preconfigured (and obfuscated) remote location where the actual content lives. This not only means that the visitor doesn't get redirected, it means that the attackers have full control over what content gets served to what visitor! In combination with this proxying, a number of variables are also sent to the backend that can be used to segment the visitor traffic, so that multiple campaigns can be run from the same files at the same time. Among these variables are:
ip(r)(x)(f) - The connecting IP address in various flavors
dom - The domain and full URL of the inserted file
ref - The HTTP referer header
prox - Is the connecting IP acting as a proxy?
agent - The user agent string
lang - Browser preferred language
Persistency on the compromised website
Perhaps the most interesting feature of this particular TDS is that it can be remotely updated by the operators. By calling the script in a specific way and supplying a key in a HTTP variable, it can overwrite itself and thus update all its code, including the remote location where the content is served. In practice this means that even if the vulnerability in the original site or plugin is fixed, the dropped files can still be managed and used until they are deleted by the site owner. Additionally, at each update slightly different obfuscation can be used to make it harder to automatically find files like these on a compromised website.
The scale of things
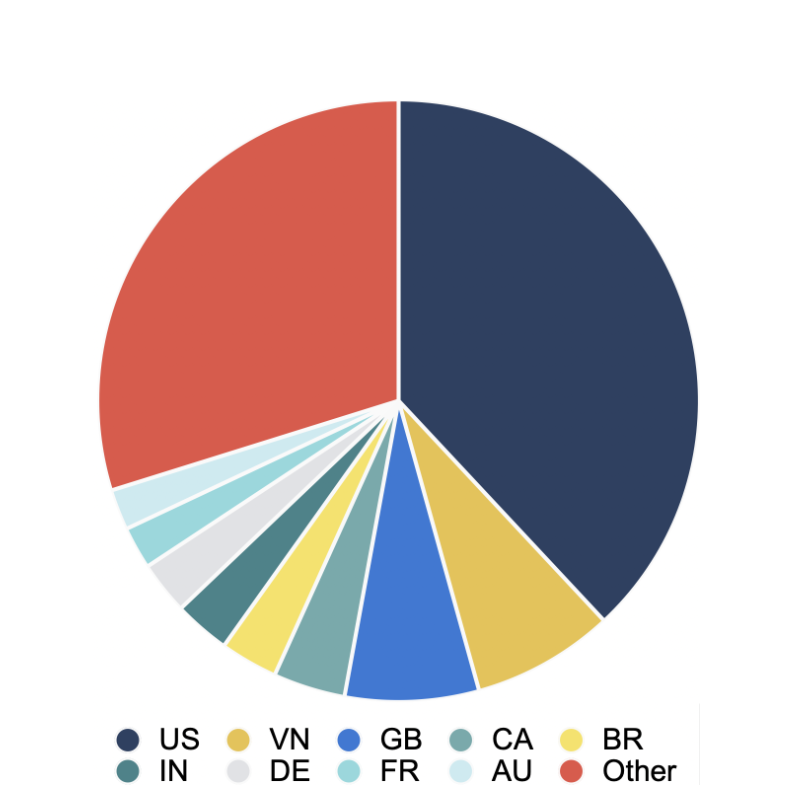
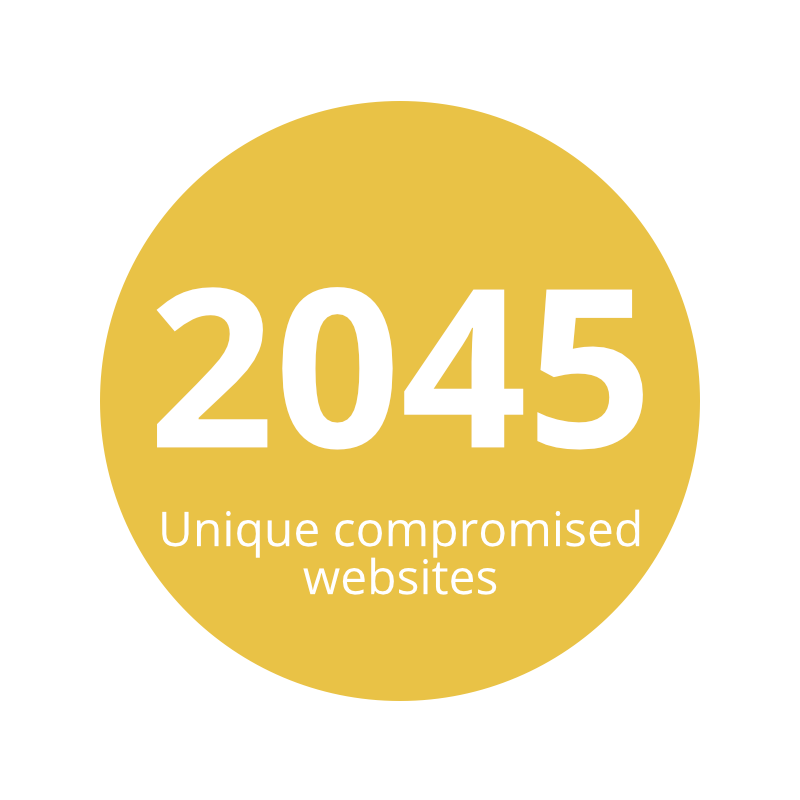
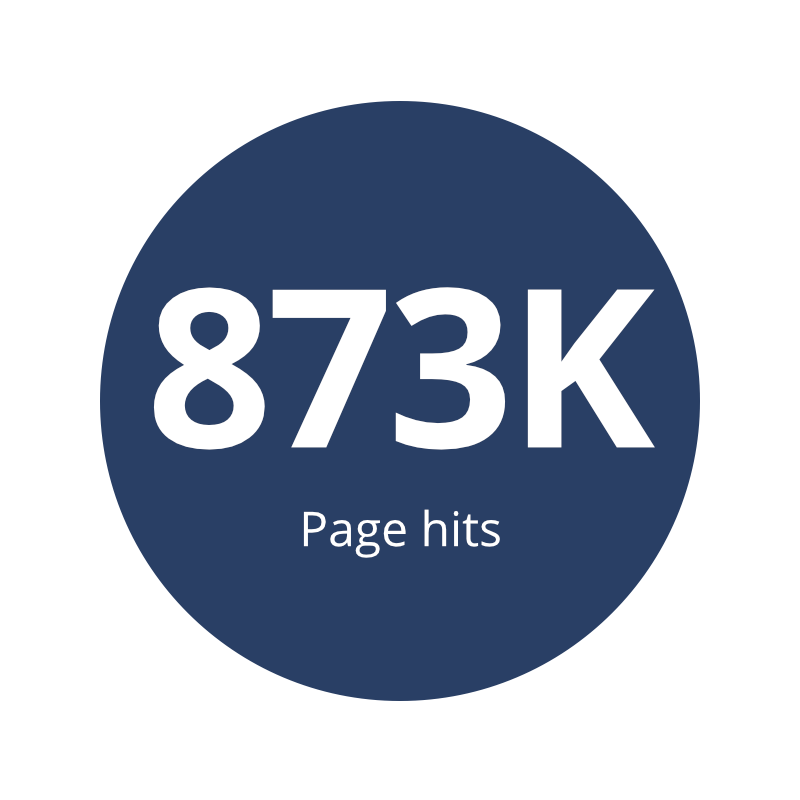
While the technical side of a TDS is interesting, another way of looking at it is how much actual traffic it gets, and where that comes from. As we investigated this particular one, we collected some numbers on various aspects of this operation, covering a 48 hour window in early May 2021:
| Country of visitors | Compromised sites feeding the TDS |
 |  |
| Traffic seen | Webservers seen |
 |  |
Furthermore:
- The content served could be divided into two categories: dating scams and bitcoin promotion.
- There seems to be no preference for particular top level domains to target or for places where the attacked websites are hosted. If it can be automatically compromised, the operators of this TDS will try it: given that the pages they inject are PHP based, if Wordpress runs, the TDS will run.
- Some visitors (around 200 distinct IP addresses) stand out quite a bit in terms of volume: these tend to be automatic URL scanners and other (web) security services.
- Among the compromised websites we found dozens of what are clearly development or staging websites. Sites like these often get forgotten with updates, or have weak login credentials.
Recommendations for website owners
While it is very hard to defend against a well funded attacker with a lot of resources, this is a somewhat lower tier of attacks. While the attacks are automated, they seem to exploit known issues with older Wordpress versions and plugins. Here's what you can do to prevent from being victimized by these kinds of attacks:
- Always keep Wordpress itself up to date
- Always keep plugins and themes up to date
- Do not use pirated versions of paid-for plugins and themes, as these can be backdoored (and if you find the plugin useful, the developers deserve your support!)
- Use strong passwords, also on staging/development websites
- If your website gets compromised, be sure to remove all files that don't belong to the software you actually use (this may require expert help).
While getting compromised by a TDS like the one we describe in this article is certainly problematic, prevention is fortunately relatively straightfoward, and uses best practices any Wordpress administrator should already be using. Stay safe, and happy blogging!
Indicators of Compromise (IOC)
Even though the files dropped through the initial exploits can change in both name and content, we found that the list of filenames used at the moment is limited and has various distinct and unusual names. If you find any files named like the ones in the list below in your Wordpress installation and the contents look obfuscated, you can assume that your Wordpress has been compromised. Wordpress itself has a good page with helpful information and links on how to fix your instance.