blog
Tracking Qbot
Qbot (aka Quakbot or Qakbot), is a piece of malware originally designed to enable bad actors to conduct financial fraud. This was done by intercepting traffic to the online banking systems of various banking institutions. Lately, it has been updated with worm-like features to help it...
In this guide
Jump to
What is Qbot?
Qbot (aka Quakbot or Qakbot), is a piece of malware originally designed to enable bad actors to conduct financial fraud. This was done by intercepting traffic to the online banking systems of various banking institutions. Lately, it has been updated with worm-like features to help it spread laterally. This update has also broadened its credential-stealing tactics to include retrieving credentials from websites that are not related to online banking.
Distribution tactics
As with lots of malware, Qbot is distributed in various ways. Predominantly we’ve observed it being dropped by Emotet infections. However, in June 2020 we have seen dedicated malspam campaigns for Qbot.
In these campaigns, the malicious payload has been in the form of a hacked server URL. If this URL is clicked by a victim it provides a zipped file containing an obfuscated VBScript that, if run, silently downloads and installs Qbot on the victim's machine.
From the beginning of June Spamhaus tracked and listed domain names that were hosting Qbot, on the Spamhaus Domain Blocklist (DBL). The malspam operation, and subsequently our tracking, ceased on June 23rd.
Qbot insights on hacked website operations
You’d be right in thinking that if you follow an URL like this:
http://www.example.com/subdir/file.zip
you would be served an actual .zip file that was present in the specified directory, right? Wrong! Qbot uses a different approach. By working together with affected website owners, Spamhaus was able to retrieve the malicious code from several hacked websites. As it turns out, compromised websites abused by Qbot host a .htaccess file containing a rewrite rule, catching all requests under /subdir/. With this approach the Qbot operators can make it seem there are different subdirectories like:
http://www.example.com/subdir/hello/donuts/file.zip
http://www.example.com/subdir/madeupdir/anotherfile.zip
http://www.example.com/subdir/yetanothernonexistantdir/thisfiledoesntexist.zip
but in reality all that traffic gets redirected by the rewrite rule to a malicious PHP script. This PHP script itself acts as a proxy, fetching the actual malicious content from a second tier of servers.
Not only does this approach allow for the creation of endless unique URLs to the malware, at the same time this obfuscation hides the real location of the malicious code on the hacked server, making mitigation by the website owners much harder. The victim who clicked on the link received in the malicious email has no clue that the file is not coming from the legit-looking URL they clicked, but instead it’s coming from somewhere else entirely.
Why did those behind this malspam campaign use this trick? Sadly we don’t have a crystal ball, but we believe these factors would have contributed to the campaign’s design:
- Apache2 & PHP requirements: Access to sites that were running apache2 and PHP were required. Since all common Content Management Systems like Wordpress or Typo3 rely on PHP, there were plenty of potential targets.
- Ability to easily access sites: As the almost endless Emotet spam campaigns have taught us, gaining access to legitimate websites is (still) all too easy. These bad actors essentially had easy access to a large number of websites, which could be compromised in bulk; deploying their malicious code.
- Low profile: Uploading relatively small file sizes enabled them to keep the lowest possible profile on the compromised websites. They created infinite bogus URLs, thus greatly reducing mitigation techniques like using antivirus signatures that are dedicated to URLs.
- Efficient deployment: The same script was used to deploy both stage 1 (the droppers, the ZIP files) and stage 2 (the actual malware). Simple, easy, efficient. What more could a cybercriminal want?
N.B. In the source code there were also instructions that set the timezone to Europe/Moscow for logging purposes. This could perhaps be an indication of the origin of the operation.
Qbot malspam
Across the campaigns the Malware Team observed, the following were used to propagate infections:
- Stolen email credentials
- Direct-to-mx connections from hacked servers
- Infected machines
It's probably worth noting that out of 480 ASNs identified during our research, the top 10 senders account for more than 66% of the total emails sent. As previously outlined, the particular method that Qbot used to distribute stage 1 droppers provided the bad actors with the ability to use a different link in each email. This is clearly illustrated in the following chart which shows that the number of individual domains (hacked websites, in this case) was consistently around 150-180 domains daily. Meanwhile, the number of unique URLs spammed was an exact match to the number of emails sent on the same day:
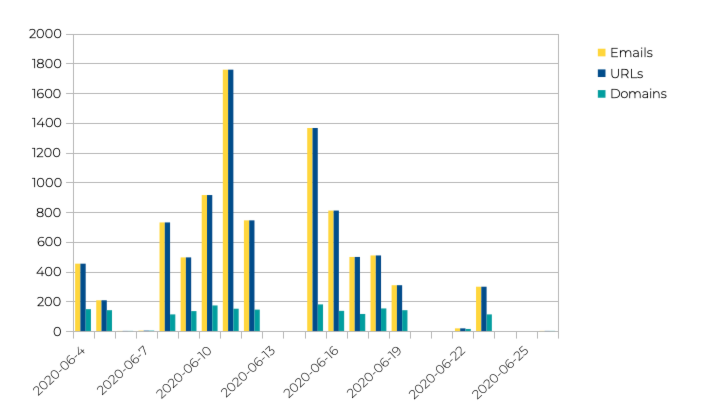
For the month of June 2020, we saw 2117 IP addresses spread over 480 AS numbers send a total of 1571 distinct domain names. In other words, during the relatively small timeframe we monitored this campaign extensively, over 1500 websites were compromised and under control of the Qbot operators.
Abuse desk responsiveness to Qbot reports
Every domain that we listed on the DBL, in relation to Qbot, was noted as ABUSED-MALWARE. This type of listing automatically generates an email to the abuse contact of the ISP and/or network that hosts the compromised web server. To review how quickly abuse desks were to neutralize these threats we tracked their response times.
The following table shows the quickest and slowest abuse desk responses, and outlines the average time taken to take down the malware:
Abuse contacts with the quickest response times:
| Abuse contact | Minutes to remove | Compromised servers |
|---|---|---|
| @jagoanhosting.com | 32 | 3 |
| @ergonet.it | 36 | 7 |
| @sprinthost.ru | 36 | 6 |
| @hostgator.com | 38 | 3 |
| @eukhost.com | 77 | 2 |
| @nic.ru | 80 | 2 |
| @nl.leaseweb.com | 81 | 2 |
| @ipipe.net | 88 | 3 |
| @ezit.hu | 96 | 3 |
| @gandi.net | 119 | 3 |
Abuse contacts with the longest response times:
| Abuse contact | Days to remove | Compromised servers |
|---|---|---|
| @rusonyx.ru | 20.8 | 3 |
| @inetmar.com | 19.5 | 2 |
| @list.alibabainc.com | 16.9 | 3 |
| @grena.ge | 16.9 | 3 |
| @hostgator.in | 16.0 | 3 |
| @voyar.net | 15.7 | 2 |
| @internetbilisim.net | 14.7 | 2 |
| @a2hosting.com | 14.0 | 9 |
| @diginl.nl | 13.5 | 7 |
| @omnilance.com | 13.2 | 2 |
Mitigation and protection
This Qbot malspam campaign is the perfect example of how the DBL can help protect your network and users from malware. While the Qbot campaign ran (June 4th - June 23rd), Spamhaus' data marked over 4.5 million queries about Qbot abused domains with a 'BAD' response, helping email administrators across the globe secure their email. All the compromised servers’ domains were listed in the DBL, so if you are using common open source products like SpamAssassin or Rspamd, you would have been automatically protected. Increased protection can be achieved by registering for a Data Query Service (DQS) account and using the dedicated Rspamd or SpamAssassin plugins.
Even though we helped block millions of Qbot malspam messages, remember that a good defense is a multi-layered defense. We recommend that you also run appropriate security measures for your operating system and don't click links in suspicious emails to download files from the internet.