blog
Spam botnets: The fall of Grum and the rise of Festi
In July 2012, FireEye in cooperation with other security organisations, such as Spamhaus, took down the Grum botnet. At that time Grum was the third largest spam-sending botnet. The event gained considerable media attention. Spamhaus worked on the takedown of the botnet by contacting...
In July 2012, FireEye in cooperation with other security organisations, such as Spamhaus, took down the Grum botnet. At that time Grum was the third largest spam-sending botnet. The event gained considerable media attention.
Spamhaus worked on the takedown of the botnet by contacting the responsible ISPs that were hosting the botnet controllers. These controllers (also known as command & control servers or C&C's) were being used by the botnet herder to control the botnet and coordinate the spam campaigns. After the command and control infrastructure of the Grum botnet had been shut down, the cybercriminals tried to re-establish their spam operation by setting up new botnet controllers. Fortunately, FireEye informed Spamhaus without any delay so that we could help shut down the new controllers quickly as well.
Since the takedowns, Spamhaus has continued to monitor the Grum botnet, which at present consists of only 150 to 500 active (spam sending) IP addresses per day. As they have no controllers, they are just operating in a true "zombie" manner. Hence, one month later we can consider the Grum botnet dead.
A few weeks before the Grum botnet was taken down, we observed a huge increase in spam activities from another spam botnet, called Festi or Spamnost by some Antivirus vendors. In June 2012, the number of active (spamming) IP addresses detected as Festi by the Spamhaus XBL was quite small compared to Grum. However, the threat landscape change rapidly by the end of June, when Festi began to show its real face. The chart below shows what had happened:
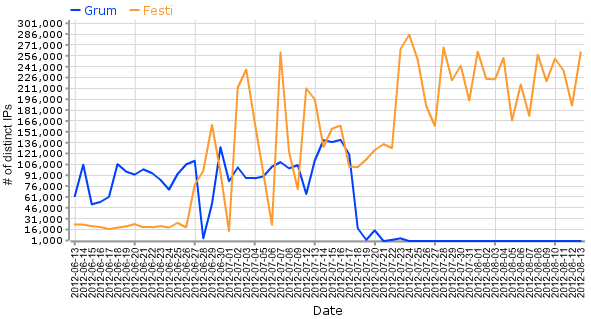
Since the beginning of July, the Spamhaus XBL has seen a huge increase in Festi spamming activities. At the peak, during one 24-hour period the XBL detected nearly 300,000 IP addresses that were infected with Festi, out of a total of 1-million that were infected with some sort of spam-sending bot. We noticed that the sheer volume of Festi spam even overwhelmed spam detection processe at some security organizations.
Since Festi started to send greater volumes of spam, it and Cutwail have been fighting for the #1 rank in the tally of the world's biggest spam botnets. The chart below compares Festi's spam activities to those of Cutwail:
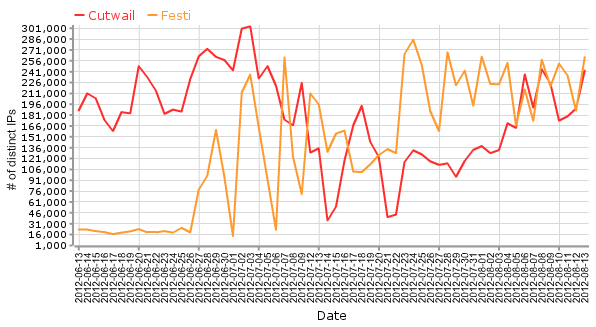
The chart shows that Grum is quite dead, but Festi has already replaced the "missing" Grum spam.
As Spamhaus' mission is to protect internet users from spam email, we will continue to monitor spam sending botnets worldwide and will provide reliable protection against this threat with Spamhaus data. In addition, Spamhaus' BGP feed (BGPf) provides protection against many kinds of botnet controllers, including those used to send spam.
References:
- Spamhaus Exploits Block List (XBL)
- About Spamhaus
- FireEye: Grum, World's Third-Largest Botnet, Knocked Down
- FireEye: Grum Recap
- FireEye: Grum - The Money Factor
- Symantec: Trojan.Spamnost
Additional reading:
- Grum: Inside The Takedown Of One Of The World’s Biggest Spam Networks* Rise and Fall of the Giant Grum Botnet* How the world's largest spam botnet was brought down* Huge spam botnet Grum is taken out by security researchers* Top Spam Botnet, “Grum,” Unplugged* Inside the Grum Botnet* Grum Botnet Bigger and More Complex Than Suspected* Could end of email spam be in sight after collapse of Grum botnet?* RSA Conference: Botnet takedowns require people, police and products