blog
Expired and exploited: Reviving a 30-year-old legacy domain for hijacking
Due to the current shortage of IPv4 addresses, any legacy IP block, regardless of its size, including Autonomous System (AS) networks, is at risk of being hijacked and misused for identity theft or other malicious activities. Here are the findings of Spamhaus' investigation into Fiberlinkcc.com, a legacy domain used to provide connectivity to hijacked IP blocks.
In this guide
Jump to
Legacy IPs: A prime target for network hijacking
It’s not uncommon for Spamhaus threat investigators to come across network assets that unauthorized third parties have hijacked for their own illegal or malicious purposes. In most cases, large IP ranges are left abandoned by their owners. This may be due to the company going out of business, losing track of IP addresses, or simply not using them.
Alarmingly, Spamhaus researchers have observed an increase in cases where the hijacked IP block was being used for internal network usage, even though reserved IP ranges are typically utilized for such purposes. No matter the reason, these IP ranges are ripe for cybercriminals to take over or “hijack.”
Fiberlinkcc.com: a victim of hijacking?
Here, we have Fiberlinkcc.com. Initial research indicates it is a normal domain, first registered in 1996 by Fiberlink Communications Corporation, a Pennsylvania-based service provider. Over the years, the business grew and was eventually acquired by IBM in 2013. As a result, the new owner no longer had a use for the domain and brand name, causing the domain to expire.
Since then, the domain has been registered by various owners until it was recently registered in 2021 by the current owner through a Russian-based registrar: nic.ru
Domain Name: FIBERLINKCC.COM
Registry Domain ID: 2612982194_DOMAIN_COM-VRSN
Registrar WHOIS Server: whois.nic.ru
Registrar URL: http://www.nic.ru
Updated Date: 2021-05-18T09:54:20Z
Creation Date: 2021-05-18T04:39:34Z
Upon closer investigation…
The domain appears to have been used to connect to several hijacked IP blocks from a Virginia data center courtesy of Cogent Communications or one of its resellers. The registration address used for this domain points to the Evoque Data Center located in Ashburn, Virginia:
network:ID:NET4-261B7A0018
network:Network-Name:NET4-261B7A0018
network:IP-Network:38.27.122.0/24
network:Org-Name:Fiberlink LLC
network:Street-Address:21571 BEAUMEADE CIRCLE
network:City:ASHBURN
network:State:VA
network:Country:US
network:Postal-Code:20147
network:Tech-Contact:ZC108-ARIN
network:Updated:2023-05-04 14:02:02
While examining the IP blocks linked to the North American businesses and organizations involved, we found the following names in the ARIN database:
- Export Development Organization - Ottawa, Ontario (Canada)
- McMillan Bathurst - Mississauga, Ontario (Canada)
- Corporate Communications, Inc. - Frisco, Texas (USA)
- TransAlta Utilities Corporation - Calgary, Alberta (Canada)
- Citigroup Inc. - Warren, New Jersey (USA)
- CoreComm Internet Services Inc - Williamsville, New York (USA)
- AT&T - Redmond, Washington (USA)
Risky business in the IP Ocean
Three companies from the above list are still in business. Unfortunately, only AT&T has identified this issue and deactivated connectivity from their hijacked IP range, 138.112.0.0/16 (see the section ‘Routing History’).
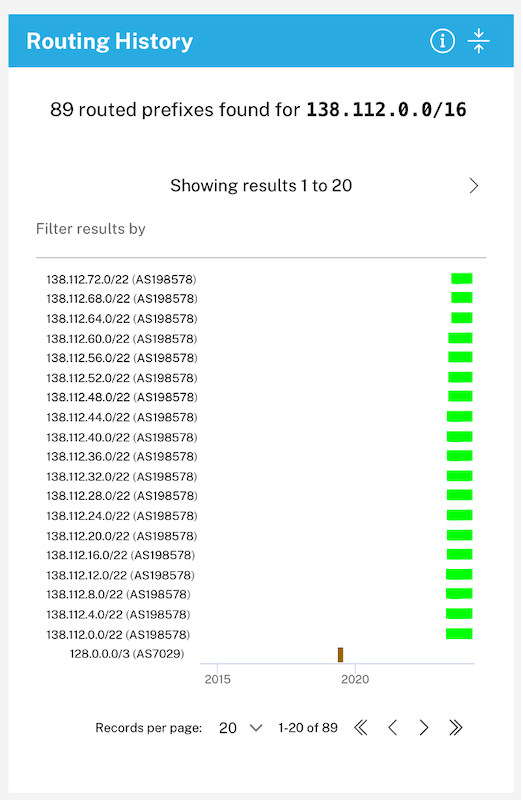
As you can see above, there has been a history of similar hijacks dating back to July 2023. Analysis of the AS numbers (ASNs) involved indicates they all trace back to a Russian service provider, IP Ocean, operated by Mamaev Anton Evgenievich. AS207967 is the single origin of all the hijacked IP ranges, which were serviced by three different AS numbers: AS52147, AS198578, and AS199598. However, as of May 6th only AS199598 remains active.
Considering IP Ocean is involved in leasing IP space, it's safe to assume the IP ranges were hijacked to be leased on this platform, possibly for nefarious purposes.
How is the situation now?
Unfortunately, the problem involving hijacked resources has not been resolved yet. Cogent Communications was notified in late March, but we have not received any response, nor has any action been taken. We invite the team at Cogent Communications to reach out to us, so that we can work together to resolve this.
There is a silver lining - we reached the owner of one of the affected IP ranges, TransAlta Corporation’s 142.152.0.0/16, which was secured through ARIN’s RPKI service. They are now in full control of this IP range and have minimized the chances of a repeat incident. We’d like to thank TransAlta for acting on our intelligence and securing this IP range.
We did receive a message from IP Ocean confirming they have permission from the IP owners to lease this IP space to their clients. However, there are still many unanswered questions: who authorized the announcement of these ranges, and what is the intended usage for these IP ranges?
Protect your network with Spamhaus DROP lists
Spamhaus' Don't Route Or Peer (DROP) lists the worst of the worst IP ranges that have been "hijacked" or leased by professional spammers, bulletproof hosters, or cyber-crime operations. Learn more about how you can protect your network with this valuable free data.