blog
Dangling DNS and the dangers of subdomain hijacking
DNS attacks are becoming increasingly prevalent, with 90% of organizations experiencing them, as per the IDC Threat Intelligence Report 2023. Due to its critical function, DNS is a frequent target for cybercrimes, including DDOS attacks, DNS spoofing and DNS hijacking. However, a lesser-known but significant threat is the dangling DNS record - read on to learn more.
In this guide
Jump to
What is a dangling DNS record?
These records are misconfigured DNS records that point to non-existent or expired services. They most often involve the CNAME (canonical name) record, which is used to alias one domain name to another. The CNAME record can be particularly useful for integrating third-party services without exposing the service provider’s domain to end-users.
Unfortunately, it’s also helpful for adversaries when hunting for neglected domains to hijack, also known as “subdomain hijacking.” This is when an attacker takes control of the external service referenced in a dangling DNS record.
Let us explain subdomain hijacking with an example.
Here we have the domain ‘spamhaus.org.’
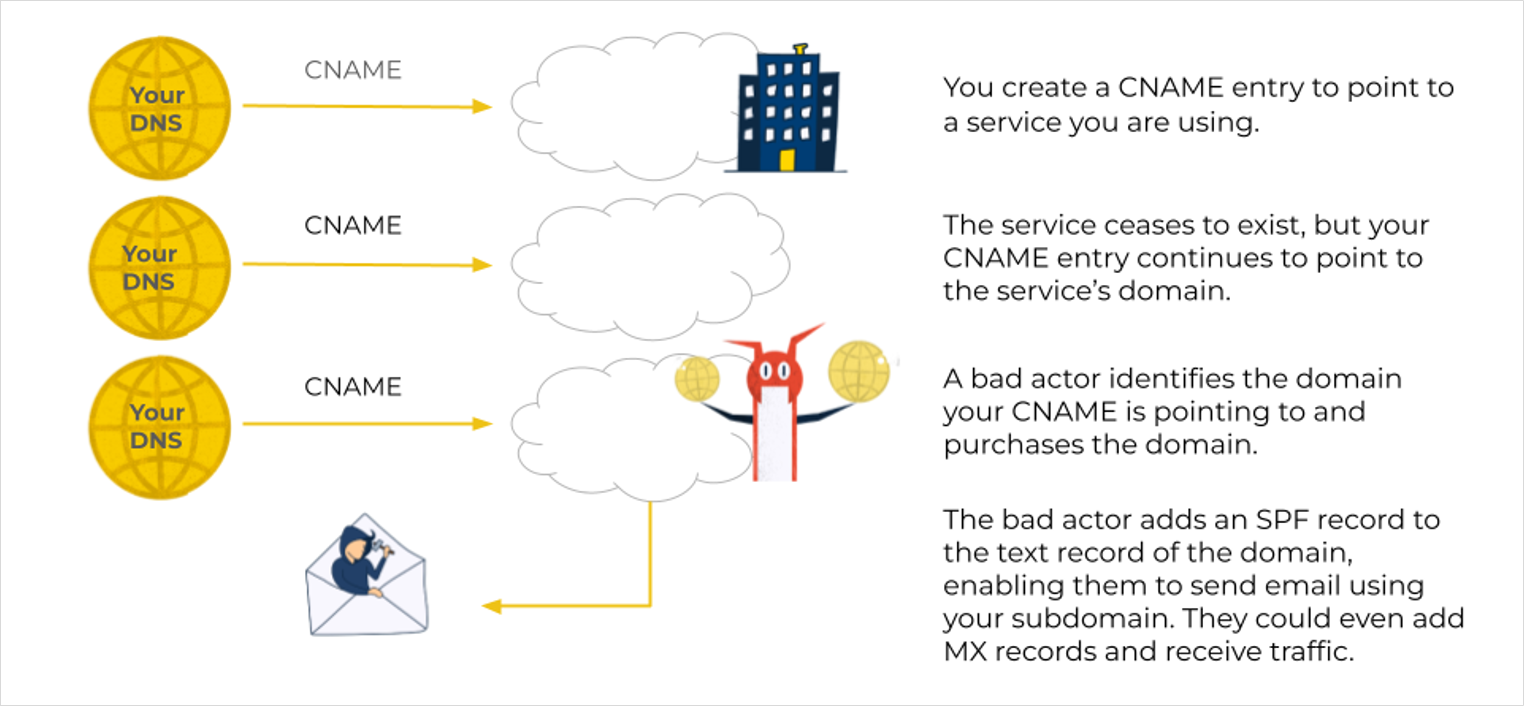
You create a CNAME entry example.spamhaus.org that points to a service you are using, ‘service.example.com.’
The service ceases to exist, but the CNAME entry example.spamhaus.org continues to point to the no-longer-existing domain, service.example.com.
This leaves the CNAME pointing to a non-existent resource, making it “dangling.”
A bad actor identifies the domain the CNAME is pointing to and purchases the domain example.com for malicious activity.
By manipulating the DNS records, bad actors can host malicious content, conduct phishing attacks, distribute malware, intercept sensitive data, and even send emails from domains they control, a tactic called “SubdoMailing.” The exploitation of SPF (Sender Policy Framework) records, is an area of particular concern.
Exploiting SPF in TXT records for hijacked domains
SPF records specify which mail servers are permitted to send email on behalf of a domain, with the aim of preventing email spoofing, where an attacker disguises themselves as a legitimate sender. However, suppose a domain has a dangling CNAME. In that case, a bad actors can exploit this vulnerability by registering the expired domain, adding an SPF record to the TXT record of the newly registered domain, enabling them to send email using your subdomain.
The process looks something like this:
Here’s where it gets interesting. Besides declaring IP addresses in an SPF record, you can also include someone else’s SPF to have them declare what IP addresses are valid. This means the SPF record of the target domain can point to other domains through the SPF include mechanism.
By manipulating the SPF record, attackers can effectively send emails from domains they don’t control, leading to phishing attacks and spreading malware. They can even add MX records and receive traffic, too!
Take the time to de-dangle your DNS
Dangling DNS typically results from poor DNS hygiene, such as failing to remove or update DNS entries. This oversight creates opportunities for attackers to redirect traffic to their own services or even gain control of a domain entirely.
To minimize risk, regularly audit and clean up your DNS. This involves the following steps:
Make sure you remove all associated records whenever services are canceled to prevent them from being reused.
Remove any unnecessary CNAMEs and ensure that the ones used point only to trusted and active domains.
Check SPF records to ensure that all included domains are actively used and under your control.
Keep track of domain expiry dates and renew or update SPF records.
Implement DMARC and DKIM for additional email authentication to add another layer of security.
By understanding the implications of dangling DNS records and the threats associated with subdomain hijacking, organizations can proactively maintain the integrity of their DNS infrastructure. Following the steps above is a good start to help prevent this issue.
Defending against SubdoMailing
To learn more about how to safeguard your DNS from threats associated with dangling DNS join Spamhaus Technology’s Carel Bitter on July 31st at 11am EDT for a panel discussion hosted by Red Sift: ‘Defending Against SubdoMailing: Strategies to Safeguard Your DNS with Spamhaus & Markmonitor.’
In this research blog, Red Sift discusses the topic of SubDoMailing in more detail.