news
Botnet Controllers in the Cloud
Cloud computing is popular these days. Millions of users consume computing power out of the cloud every day. Cloud computing comes with several advantages over traditional server hosting, such as scalability and quick deployment of new resources. As of January 2017, several large botnet operators appear to have discovered the...
In this guide
Jump to
Cloud computing is popular these days. Millions of users consume computing power out of the cloud every day. Cloud computing comes with several advantages over traditional server hosting, such as scalability and quick deployment of new resources.
As of January 2017, several large botnet operators appear to have discovered the benefits of cloud computing as well, and have started to deploy their botnet controllers in the cloud.
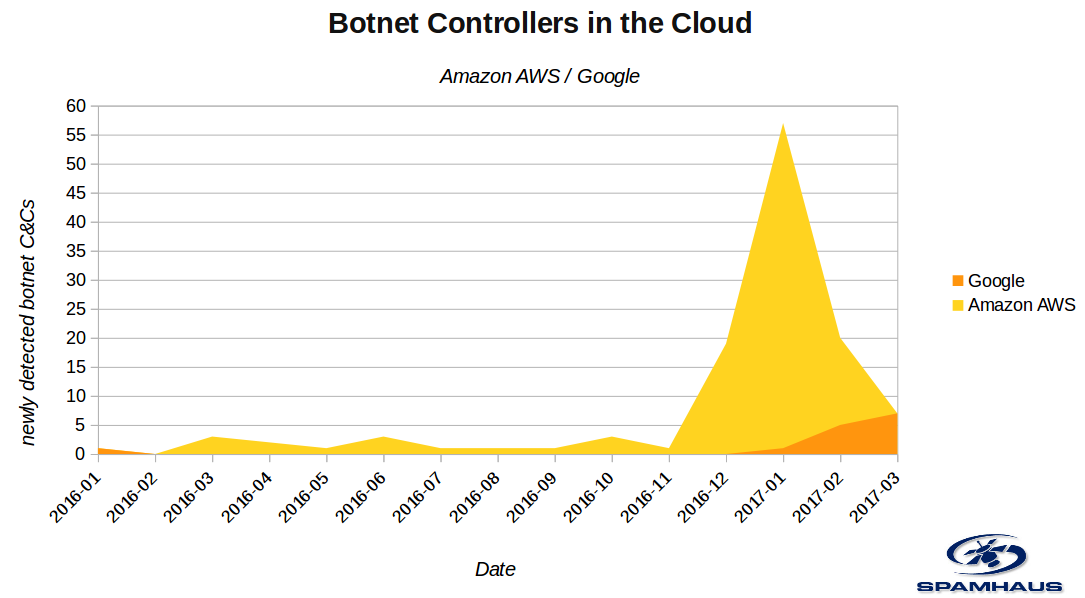
Since early 2017, we at Spamhaus have seen a significant increase in the number of botnet controllers (botnet command and control servers, C&C, C2) popping up at legitimate cloud computing providers. Most have been at Amazon's Cloud Computing platform "AWS" but we have recently seen an increase in new botnet controllers hosted on Google's Cloud Computing platform "Compute Engine". The chart below documents the numbers of newly detected botnet controllers at Amazon AWS and Google Compute Engine.
Discussion
This chart is based only on botnet controllers. It does not include other fraudulent infrastructure, such as payment sites for ransomware (TorrentLocker, Locky, Cerber etc) or malware distribution sites. We have seen a spike in those types of criminal infrastructure at Amazon and Google as well.
Neither Amazon nor Google are handling abuse reports about botnet controllers, malware distribution sites, and other types of criminal activity on their clouds in a timely manner. Both allow botnet controllers to remain online for weeks at a time, despite multiple abuse reports and reminders.
Spamhaus has reached out repeatedly to both Amazon and Google about these abuse problems, but has received no relevant response from either so far.
As we are lacking any useful feedback from Amazon and Google on the causes of these ongoing abuse problems, we can only speculate. Previous experience with issues at cloud providers suggest that a weak or non-existent customer verification process might be the root cause of these abuse problems. Other factors which could lead to such problems include a weak Acceptable Use Policy, or a corporate culture and management not supporting of Abuse Desk policy enforcement.
We encourage Amazon and Google to take the appropriate actions to stop all outstanding abuse problems on their networks, just as all responsible hosting networks must do. These are the specific issues which we are presently tracking at those networks:
Open SBL Advisories in the responsibility of amazon.com:
https://www.spamhaus.org/sbl/listings/amazon.com
Open SBL Advisories in the responsibility of google.com:
https://www.spamhaus.org/sbl/listings/google.com
In addition, Amazon and Google must take necessary and appropriate steps to prevent further abuse of all types from being generated on their network. That includes reacting to abuse reports from many sources including, but not limited to, SBL listings, and effectively prohibiting all services to spammers and other abusive users.
We at Spamhaus are continuing to monitor the situations at Amazon AWS and Google Compute Engine, and may take additional action(s) to protect Spamhaus users from further abuse generated on those networks. We are by no means happy to publish a complaint of this nature against two such established Internet companies, yet at this time we are very concerned about the ongoing abuse tolerated by networks which should be setting reputational standards for legitimate hosting, and not for supporting botnets.
Further reading
How hosting providers can battle fraudulent sign-ups:
https://www.spamhaus.org/news/article/687/how-hosting-providers-can-battle-fraudulent-sign-ups
Spamhaus Botnet Summary 2016:
https://www.spamhaus.org/news/article/733/spamhaus-botnet-summary-2016
M3AAWG Hosting Best Practices 2015
https://www.m3aawg.org/sites/default/files/document/M3AAWG_Hosting_Abuse_BCPs-2015-03.pdf
Update 2017-05-06 04:17 UTC
We are in contact with appropriate Security and Abuse personnel at Amazon. They are aware of Amazon's SBL listings and they are attempting to stop the problems. Unfortunately, at this time there are still botnet controllers active more than 24 hours after notification, and snowshoe spammers are rampant on AWS cloud ranges. Amazon has requested additional information regarding some SBL records. While ongoing efforts are needed to curtail abuse of its hosting space, Spamhaus appreciates Amazon's efforts to resolve those issues and we are happy to process SBL removals as we receive them.
Communication status with Google Abuse and Security personnel remains a concern. Botnet controller, phish, spam and carder sites remain active long after notification. Google, please respond!
Update 2017-05-12 23:50 UTC
Thank you for responding, Google, we look forward to resolving the outstanding SBL issues.
««»»