news
A surge of malvertising across Google Ads is distributing dangerous malware
Recently, researchers have witnessed a massive spike affecting famous brands, with multiple malware being utilized. This is not “the norm.” Here’s what researchers are observing and a theory on this tsunami of abuse.
In this guide
Jump to
Threat researchers are used to seeing a moderate flow of malvertising via Google Ads. However, over the past few days, researchers have witnessed a massive spike affecting numerous famous brands, with multiple malware being utilized. This is not “the norm”. Here’s what researchers are observing and a theory (yet to be proven) on this tsunami of abuse.
A ramp-up in malvertising activity
Search “google ads malvertising”, and a plethora of articles published over the past few weeks will be listed. With headlines like IcedID spreads via malvertising, from CyberWire, to Hackers abuse Google Ads to spread malware in legit software, from Bleeping Computer.
Numerous malware, including AuroraStealer, IcedID, Meta Stealer, RedLine Stealer, and Vidar are being delivered to victims’ machines through bad actors impersonating brands such as Adobe Reader, Gimp, Microsoft Teams, OBS, Slack, and Thunderbird using Google Ads.
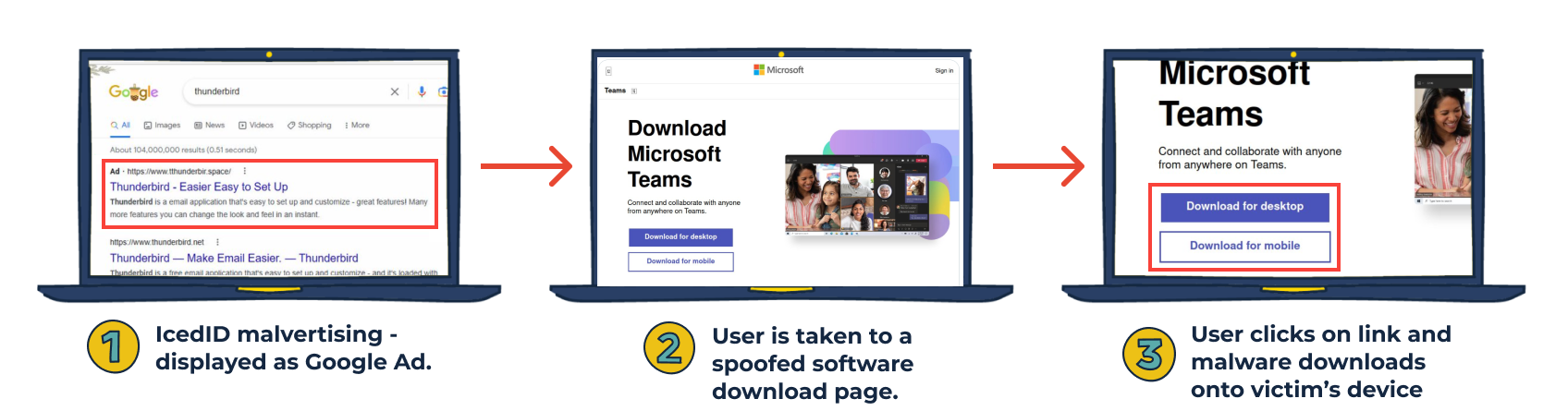
What abuse are we seeing?
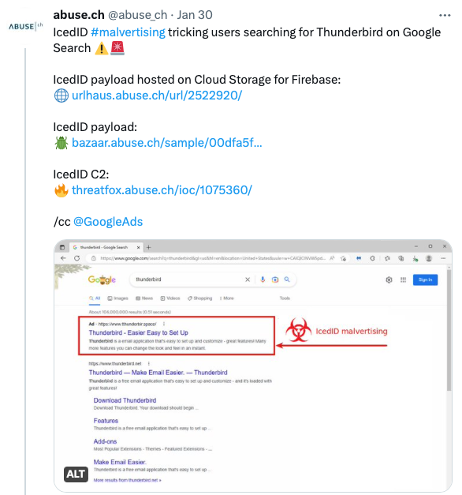
Spamhaus Technology’s partner abuse.ch and The Spamhaus Project are both observing a significant increase in this activity. On January 30th, abuse.ch reported on Twitter that victims were being lured with impersonator Thunderbird Google Ads, leading to spoofed pages, which, once clicked on, delivered an IcedID payload to the unwitting victim’s device.
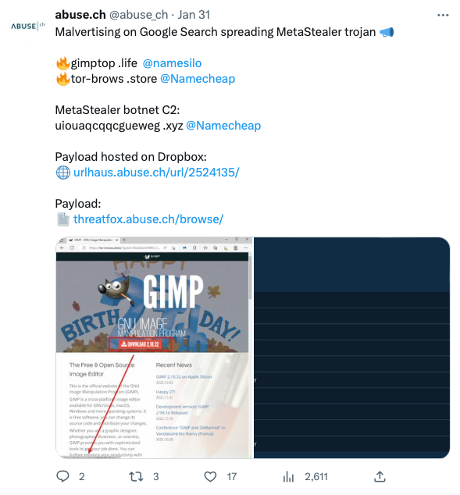
One day later, Google Ads was being used to spread the MetaStealer trojan:
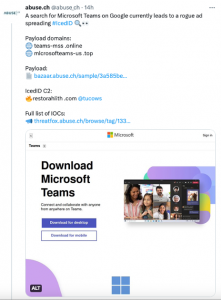
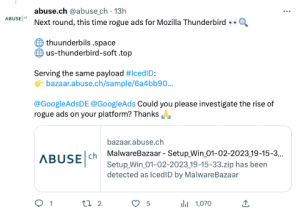
Over the past 24 hours, both Mozilla Thunderbird and Microsoft teams have been impersonated, with IcedID malware being delivered. It’s evident that despite usually focusing on malspam, the operators of IcedID have turned their attention(s) to malvertising.
Meanwhile, The Spamhaus Project researchers have various intelligence relating to this spate of Google Ad malvertising, including lookalike Nvidia domains such as:
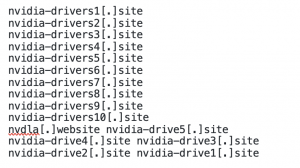
Spamhaus researchers have linked fake Nvidia domains with Aurora Stealer and Vidar malware. Some of the Google Ads purposefully have typos, which we presume is to try and evade detection, for example:
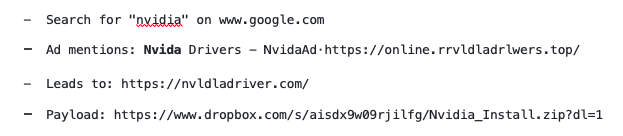
What could be causing this escalation?
The founder of abuse.ch believes, “It is likely that a threat actor has started to sell malvertising as a service on the dark web, and there is a great deal of demand.” They explained they’re observing “different infrastructure being used in these ads, spreading different malware families.” This leads to the conclusion that “ad serving” is a service that threat actors purchase.
Additionally, the research teams are simultaneously seeing two rogue ads appearing for the exact search term but spreading different malware families – this is another pointer toward the fact this is malvertising as a service.
A plea to Google Ads
The Spamhaus Project’s domain expert, Carel Bitter, questioned why Google Ads approved adverts linking to new domains. Throughout the security industry, the immediate use of newly registered domains is associated with high-risk activity. If you take a look at the WHOIS data for one of the Nvidia lookalike domains, it was created less than a week ago:
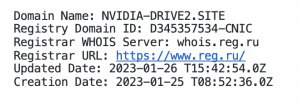
Carel acknowledges that he’s an expert on domains, not Google Ads security – we’d love to hear from you if you have detailed knowledge in this area and can help us understand why Google is allowing the use of recently registered domains.
In the meantime, we hope Google Ads can rapidly quash this wave of malicious behavior across their platform.